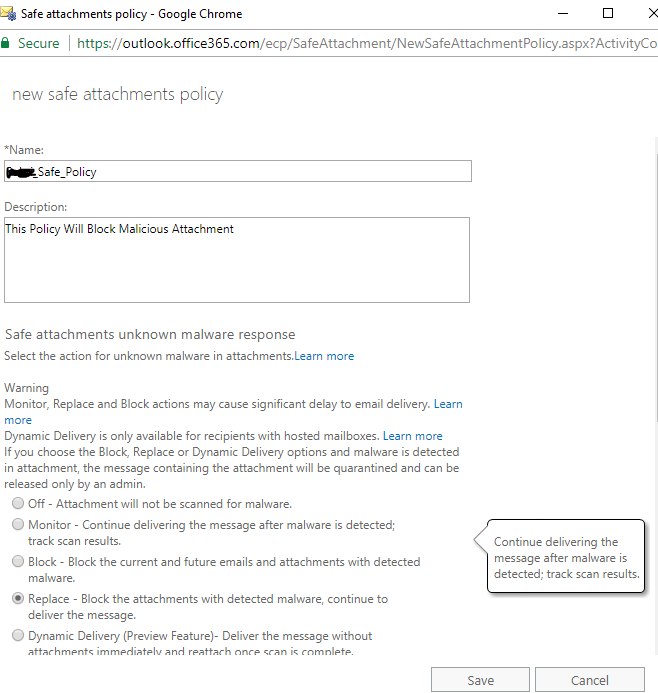
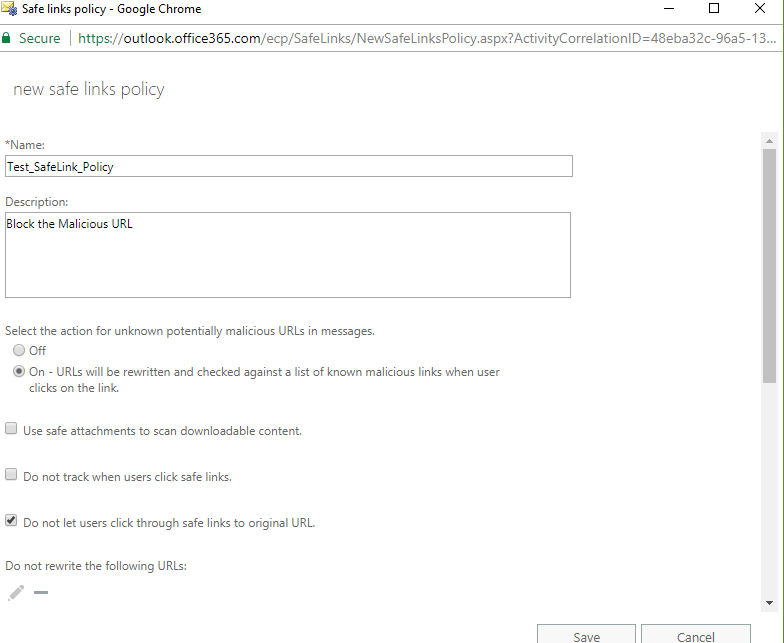
We installed Exchange 2016 for Co-Existence with Exchange 2010. Configured the Exchange 2016 Virtual directories, We were testing the Outlook anywhere and found that the internal Exchange 2010 users are unable to connect to Exchange while new created Exchange 2016 users could connect fine with there Outlook clients.
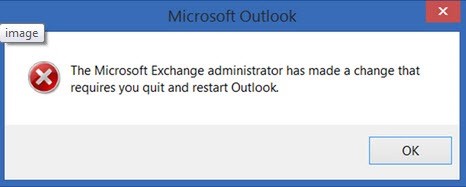
We were getting outlook is disconnected. But OWA and Active sync was working fine.
- We have checked outlook anywhere configuration which seems to be fine.
- Checked the name from the internal access point for Outlook.
- Get-OutlookAnywhere -Identity “exch2016-01\Rpc (Default Web site)” | select InternalHostname
- Checked the name from the CAS Array on your Exchange 2010 with following Cmd:
- Get-ClientAccessArray | Select Fqdn
- Checked RpcClientAccessServer is set on the Exchange 2010 Mailbox Databases
- Get-MailboxDatabase | Select Name, RPCClientAccessServer
RPC Client Access Arra/Server and the internal Outlook Anywhere names were the same, that caused a routing loop once we switched over the default namespace to Exchange 2016.
So we fixed this name issue with below cmd.
Set-MailboxDatabase –Identity “<Database Name>” –RPCClientAccessServer “exch2010-01.contoso.local”
in relation to the end-user. Changing this setting results in end-users getting pop-ups in Outlook stating that an Exchange Administration has changed settings and that Outlook must be closed in re-opened.